Category
Threat Intelligence
Elastic Security Labs detected the recent emergence of infostealers using an illicitly acquired version of the commercial evasion framework, SHELLTER, to deploy post-exploitation payloads.

From South America to Southeast Asia: The Fragile Web of REF7707
REF7707 targeted a South American foreign ministry using novel malware families. Inconsistent evasion tactics and operational security missteps exposed additional adversary-owned infrastructure.

Betting on Bots: Investigating Linux malware, crypto mining, and gambling API abuse
The REF6138 campaign involved cryptomining, DDoS attacks, and potential money laundering via gambling APIs, highlighting the attackers' use of evolving malware and stealthy communication channels.

Code of Conduct: DPRK’s Python-fueled intrusions into secured networks
Investigating the DPRK’s strategic use of Python and carefully crafted social engineering, this publication sheds light on how they breach highly secure networks with evolving and effective cyber attacks.

GrimResource - Microsoft Management Console for initial access and evasion
Elastic researchers uncovered a new technique, GrimResource, which allows full code execution via specially crafted MSC files. It underscores a trend of well-resourced attackers favoring innovative initial access methods to evade defenses.

Globally distributed stealers
This article describes our analysis of the top malware stealer families, unveiling their operation methodologies, recent updates, and configurations. By understanding the modus operandi of each family, we better comprehend the magnitude of their impact and can fortify our defences accordingly.

Invisible miners: unveiling GHOSTENGINE’s crypto mining operations
Elastic Security Labs has identified REF4578, an intrusion set incorporating several malicious modules and leveraging vulnerable drivers to disable known security solutions (EDRs) for crypto mining.
Sinking macOS Pirate Ships with Elastic Behavior Detections
This research looks at a recently found macOS malware campaign using the macOS Endpoint Security Framework paired with the Elastic Agent to hunt and detect the behaviors this malware exhibits.

PIKABOT, I choose you!
Elastic Security Labs observed new PIKABOT campaigns, including an updated version. PIKABOT is a widely deployed loader malicious actors utilize to distribute additional payloads.

Unmasking a Financial Services Intrusion: REF0657
Elastic Security Labs details an intrusion leveraging open-source tooling and different post-exploitation techniques targeting the financial services industry in South Asia.

Elastic catches DPRK passing out KANDYKORN
Elastic Security Labs exposes an attempt by the DPRK to infect blockchain engineers with novel macOS malware.
GHOSTPULSE haunts victims using defense evasion bag o' tricks
Elastic Security Labs reveals details of a new campaign leveraging defense evasion capabilities to infect victims with malicious MSIX executables.

Disclosing the BLOODALCHEMY backdoor
BLOODALCHEMY is a new, actively developed, backdoor that leverages a benign binary as an injection vehicle, and is a part of the REF5961 intrusion set.

Introducing the REF5961 intrusion set
The REF5961 intrusion set discloses three new malware families targeting ASEAN members. The threat actor leveraging this intrusion set continues to develop and mature their capabilities.

The DPRK strikes using a new variant of RUSTBUCKET
Watch out! We’ve recently discovered a variant of RUSTBUCKET. Read this article to understand the new capabilities we’ve observed, as well as how to identify it in your own network.

Initial research exposing JOKERSPY
Explore JOKERSPY, a recently discovered campaign that targets financial institutions with Python backdoors. This article covers reconnaissance, attack patterns, and methods of identifying JOKERSPY in your network.

Elastic charms SPECTRALVIPER
Elastic Security Labs has discovered the P8LOADER, POWERSEAL, and SPECTRALVIPER malware families targeting a national Vietnamese agribusiness. REF2754 shares malware and motivational elements of the REF4322 and APT32 activity groups.

Attack chain leads to XWORM and AGENTTESLA
Our team has recently observed a new malware campaign that employs a well-developed process with multiple stages. The campaign is designed to trick unsuspecting users into clicking on the documents, which appear to be legitimate.

REF2924: how to maintain persistence as an (advanced?) threat
Elastic Security Labs describes new persistence techniques used by the group behind SIESTAGRAPH, NAPLISTENER, and SOMNIRECORD.

PHOREAL Malware Targets the Southeast Asian Financial Sector
Elastic Security discovered PHOREAL malware, which is targeting Southeast Asia financial organizations, particularly those in the Vietnamese financial sector.

Update to the REF2924 intrusion set and related campaigns
Elastic Security Labs is providing an update to the REF2924 research published in December of 2022. This update includes malware analysis of the implants, additional findings, and associations with other intrusions.

SiestaGraph: New implant uncovered in ASEAN member foreign ministry
Elastic Security Labs is tracking likely multiple on-net threat actors leveraging Exchange exploits, web shells, and the newly discovered SiestaGraph implant to achieve and maintain access, escalate privilege, and exfiltrate targeted data.

Exploring the REF2731 Intrusion Set
The Elastic Security Labs team has been tracking REF2731, an 5-stage intrusion set involving the PARALLAX loader and the NETWIRE RAT.

Operation Bleeding Bear
Elastic Security verifies new destructive malware targeting Ukraine: Operation Bleeding Bear

Doing time with the YIPPHB dropper
Elastic Security Labs outlines the steps collect and analyze the various stages of the REF4526 intrusion set. This intrusion set uses a creative approach of Unicode icons in Powershell scripts to install a loader, a dropper, and RAT implants.

ICEDIDs network infrastructure is alive and well
Elastic Security Labs details the use of open source data collection and the Elastic Stack to analyze the ICEDID botnet C2 infrastructure.

CUBA Ransomware Campaign Analysis
Elastic Security observed a ransomware and extortion campaign leveraging a combination of offensive security tools, LOLBAS, and exploits to deliver the CUBA ransomware malware.

LUNA Ransomware Attack Pattern Analysis
In this research publication, we'll explore the LUNA attack pattern — a cross-platform ransomware variant.

Exploring the QBOT Attack Pattern
In this research publication, we'll explore our analysis of the QBOT attack pattern — a full-featured and prolific malware family.

Elastic Security uncovers BLISTER malware campaign
Elastic Security has identified active intrusions leveraging the newly identified BLISTER malware loader utilizing valid code-signing certificates to evade detection. We are providing detection guidance for security teams to protect themselves.

A close look at the advanced techniques used in a Malaysian-focused APT campaign
Our Elastic Security research team has focused on advanced techniques used in a Malaysian-focused APT campaign. Learn who’s behind it, how the attack works, observed MITRE attack® techniques, and indicators of compromise.

Playing defense against Gamaredon Group
Learn about the recent campaign of a Russia-based threat group known as Gamaredon Group. This post will review these details and provide detection strategies.

FORMBOOK Adopts CAB-less Approach
Campaign research and analysis of an observed FORMBOOK intrusion attempt.
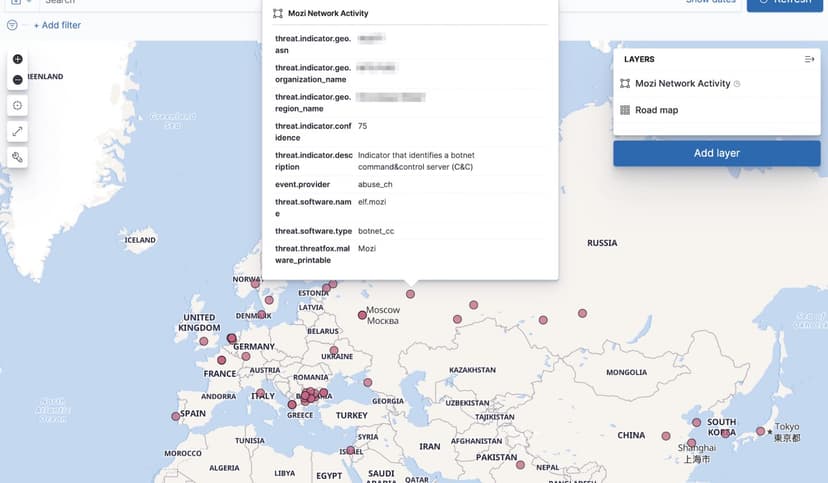
Collecting and operationalizing threat data from the Mozi botnet
The Mozi botnet is an ongoing malware campaign targeting unsecured and vulnerable networking devices. This post will showcase the analyst journey of collecting, analyzing, and operationalizing threat data from the Mozi botnet.
Okta and LAPSUS$: What you need to know
The latest organization under the microscope of the LAPSUS$ group is Okta. Threat hunt for the recent breach targeting Okta users using these simple steps in Elastic
Ransomware, interrupted: Sodinokibi and the supply chain
Learn how Elastic Endpoint Security's behavior-based protections prevented a targeted ransomware attack on multiple endpoints.
