Author
Daniel Stepanic
Elastic Security Labs Team Principal Security Researcher, Malware
Articles

BADIIS to the Bone: New Insights to a Global SEO Poisoning Campaign
In November 2025, Elastic Security Labs observed an intrusion affecting a multinational organization based in Southeast Asia. During the analysis of this activity, our team observed various post-compromise techniques and tooling used to deploy BADIIS malware onto a Windows web server consistent with other industry publications.

NANOREMOTE, cousin of FINALDRAFT
The fully-featured backdoor we call NANOREMOTE shares characteristics with malware described in REF7707 and is similar to the FINALDRAFT implant.

TOLLBOOTH: What's yours, IIS mine
REF3927 abuses publicly disclosed ASP.NET machine keys to compromise IIS servers and deploy TOLLBOOTH SEO cloaking modules globally.

WARMCOOKIE One Year Later: New Features and Fresh Insights
A year later: Elastic Security Labs re-examines the WARMCOOKIE backdoor.

Taking SHELLTER: a commercial evasion framework abused in-the-wild
Elastic Security Labs detected the recent emergence of infostealers using an illicitly acquired version of the commercial evasion framework, SHELLTER, to deploy post-exploitation payloads.

De-obfuscating ALCATRAZ
An exploration of techniques used by the obfuscator ALCATRAZ.

You've Got Malware: FINALDRAFT Hides in Your Drafts
During a recent investigation (REF7707), Elastic Security Labs discovered new malware targeting a foreign ministry. The malware includes a custom loader and backdoor with many features including using Microsoft’s Graph API for C2 communications.

Under the SADBRIDGE with GOSAR: QUASAR Gets a Golang Rewrite
Elastic Security Labs share details about the SADBRIDGE loader and GOSAR backdoor, malware used in campaigns targeting Chinese-speaking victims.

Katz and Mouse Game: MaaS Infostealers Adapt to Patched Chrome Defenses
Elastic Security Labs breaks down bypass implementations from the infostealer ecosystem’s reaction to Chrome 127's Application-Bound Encryption scheme.

BITS and Bytes: Analyzing BITSLOTH, a newly identified backdoor
Elastic Security Labs identified a novel Windows backdoor leveraging the Background Intelligent Transfer Service (BITS) for C2. This malware was found during a recent activity group tracked as REF8747.

Dipping into Danger: The WARMCOOKIE backdoor
Elastic Security Labs observed threat actors masquerading as recruiting firms to deploy a new malware backdoor called WARMCOOKIE. This malware has standard backdoor capabilities, including capturing screenshots, executing additional malware, and reading/writing files.

Globally distributed stealers
This article describes our analysis of the top malware stealer families, unveiling their operation methodologies, recent updates, and configurations. By understanding the modus operandi of each family, we better comprehend the magnitude of their impact and can fortify our defences accordingly.

Spring Cleaning with LATRODECTUS: A Potential Replacement for ICEDID
Elastic Security Labs has observed an uptick in a recent emerging loader known as LATRODECTUS. This lightweight loader packs a big punch with ties to ICEDID and may turn into a possible replacement to fill the gap in the loader market.

PIKABOT, I choose you!
Elastic Security Labs observed new PIKABOT campaigns, including an updated version. PIKABOT is a widely deployed loader malicious actors utilize to distribute additional payloads.

Unmasking a Financial Services Intrusion: REF0657
Elastic Security Labs details an intrusion leveraging open-source tooling and different post-exploitation techniques targeting the financial services industry in South Asia.

Getting gooey with GULOADER: deobfuscating the downloader
Elastic Security Labs walks through the updated GULOADER analysis countermeasures.

Dancing the night away with named pipes - PIPEDANCE client release
In this publication, we will walk through this client application’s functionality and how to get started with the tool.

Introducing the REF5961 intrusion set
The REF5961 intrusion set discloses three new malware families targeting ASEAN members. The threat actor leveraging this intrusion set continues to develop and mature their capabilities.

Revisiting BLISTER: New development of the BLISTER loader
Elastic Security Labs dives deep into the recent evolution of the BLISTER loader malware family.

Elastic charms SPECTRALVIPER
Elastic Security Labs has discovered the P8LOADER, POWERSEAL, and SPECTRALVIPER malware families targeting a national Vietnamese agribusiness. REF2754 shares malware and motivational elements of the REF4322 and APT32 activity groups.

Elastic Security Labs discovers the LOBSHOT malware
Elastic Security Labs is naming a new malware family, LOBSHOT. LOBSHOT propagates and infiltrates targeted networks through Google Ads and hVNC sessions to deploy backdoors masquerading as legitimate application installers.
Elastic users protected from SUDDENICON’s supply chain attack
Elastic Security Labs is releasing a triage analysis to assist 3CX customers in the initial detection of SUDDENICON, a potential supply-chain compromise affecting 3CX VOIP softphone users.

BLISTER Loader
The BLISTER loader continues to be actively used to load a variety of malware.

Thawing the permafrost of ICEDID Summary
Elastic Security Labs analyzed a recent ICEDID variant consisting of a loader and bot payload. By providing this research to the community end-to-end, we hope to raise awareness of the ICEDID execution chain, capabilities, and design.

PHOREAL Malware Targets the Southeast Asian Financial Sector
Elastic Security discovered PHOREAL malware, which is targeting Southeast Asia financial organizations, particularly those in the Vietnamese financial sector.

Twice around the dance floor - Elastic discovers the PIPEDANCE backdoor
Elastic Security Labs is tracking an active intrusion into a Vietnamese organization using a recently discovered triggerable, multi-hop backdoor we are calling PIPEDANCE. This full-featured malware enables stealthy operations through the use of named

FLARE-ON 9 Solutions:
This year's FLARE-ON consisted of 11 different reverse engineering challenges with a range of interesting binaries. We really enjoyed working on these challenges and have published our solutions here to Elastic Security Labs.

SiestaGraph: New implant uncovered in ASEAN member foreign ministry
Elastic Security Labs is tracking likely multiple on-net threat actors leveraging Exchange exploits, web shells, and the newly discovered SiestaGraph implant to achieve and maintain access, escalate privilege, and exfiltrate targeted data.

Exploring the REF2731 Intrusion Set
The Elastic Security Labs team has been tracking REF2731, an 5-stage intrusion set involving the PARALLAX loader and the NETWIRE RAT.

Operation Bleeding Bear
Elastic Security verifies new destructive malware targeting Ukraine: Operation Bleeding Bear

Detection rules for SIGRed vulnerability
The SIGRed vulnerability impacts all systems leveraging the Windows DNS server service (Windows 2003+). To defend your environment, we recommend implementing the detection logic included in this blog post using technology like Elastic Security.

ICEDIDs network infrastructure is alive and well
Elastic Security Labs details the use of open source data collection and the Elastic Stack to analyze the ICEDID botnet C2 infrastructure.

Elastic protects against data wiper malware targeting Ukraine: HERMETICWIPER
Analysis of the HERMETICWIPER malware targeting Ukranian organizations.
Extracting Cobalt Strike Beacon Configurations
Part 2 - Extracting configurations from Cobalt Strike implant beacons.

CUBA Ransomware Campaign Analysis
Elastic Security observed a ransomware and extortion campaign leveraging a combination of offensive security tools, LOLBAS, and exploits to deliver the CUBA ransomware malware.

LUNA Ransomware Attack Pattern Analysis
In this research publication, we'll explore the LUNA attack pattern — a cross-platform ransomware variant.

A close look at the advanced techniques used in a Malaysian-focused APT campaign
Our Elastic Security research team has focused on advanced techniques used in a Malaysian-focused APT campaign. Learn who’s behind it, how the attack works, observed MITRE attack® techniques, and indicators of compromise.

Playing defense against Gamaredon Group
Learn about the recent campaign of a Russia-based threat group known as Gamaredon Group. This post will review these details and provide detection strategies.
Going Coast to Coast - Climbing the Pyramid with the Deimos Implant
The Deimos implant was first reported in 2020 and has been in active development; employing advanced analysis countermeasures to frustrate analysis. This post details the campaign TTPs through the malware indicators.

FORMBOOK Adopts CAB-less Approach
Campaign research and analysis of an observed FORMBOOK intrusion attempt.
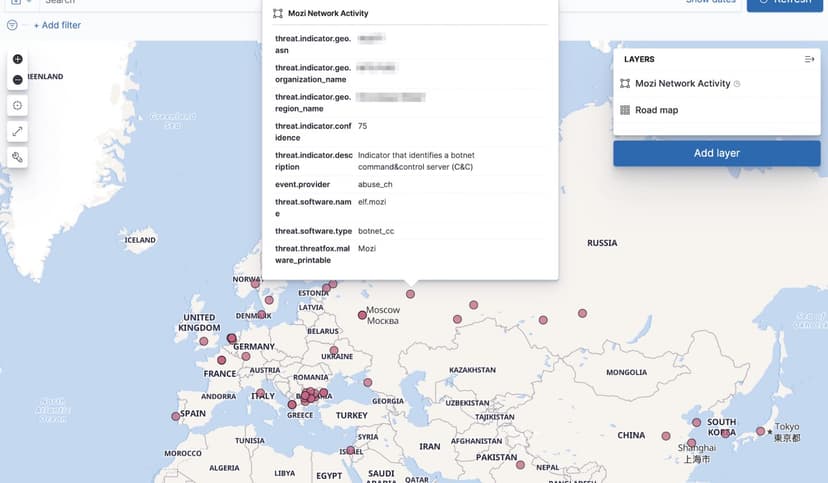
Collecting and operationalizing threat data from the Mozi botnet
The Mozi botnet is an ongoing malware campaign targeting unsecured and vulnerable networking devices. This post will showcase the analyst journey of collecting, analyzing, and operationalizing threat data from the Mozi botnet.
Detection and response for the actively exploited ProxyShell vulnerabilities
In the last week, Elastic Security has observed the exploitation of Microsoft Exchange vulnerabilities associated with ProxyShell. Review the post to find newly released details about this activity.
Collecting Cobalt Strike Beacons with the Elastic Stack
Part 1 - Processes and technology needed to extract Cobalt Strike implant beacons

Embracing offensive tooling: Building detections against Koadic using EQL
Find new ways to build behavioral detections against post-exploitation frameworks such as Koadic using Event Query Language (EQL).